Crash Override finds AI-generated code, so you can accelerate adoption and secure it.
Book a DemoSubscribe to our newsletterAI tools are genuinely transformative, letting developers ship better software, faster, and cheaper. But, that only works if you still care deeply about quality, ownership, and actually understanding what’s running. Crash Override gives you the visibility, traceability, and code-to-cloud context—right where developers already live, letting the move quickly, safely, and securely.
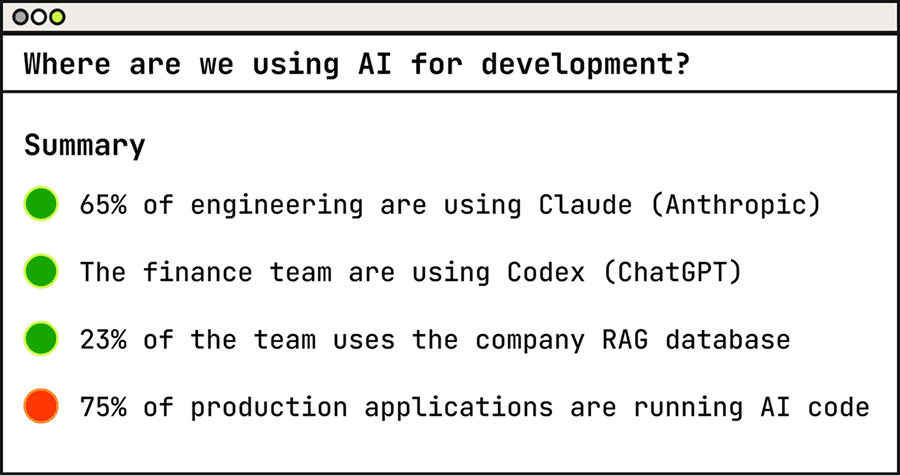
Know which AI tools developers are using, where AI-generated code is being deployed, and which teams are adopting it.

Expand AI adoption across teams, measure impact, and optimize usage to drive real productivity gains.

Give security the visibility and controls to manage AI risk, so more teams can adopt AI safely and confidently.
Lack of clear code ownership is a persistent challenge in modern software development. Crash Override offers a practical path to addressing that gap without disrupting developer workflows.

